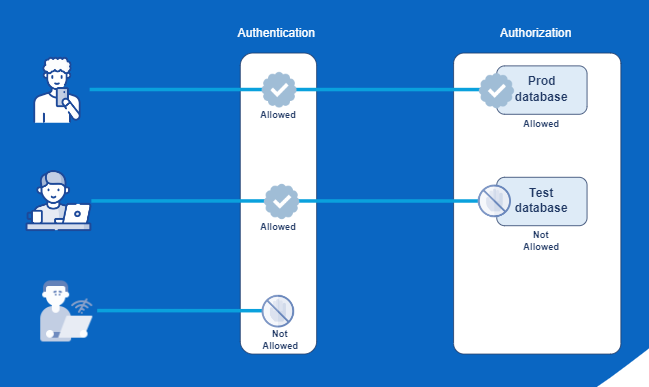
In any company that thrives on IT, where infrastructure resources often grow uncontrollably, server consolidation is becoming not just a […]
Currently browsing: IT Guide
WIN10 END OF LIFE. End of support for Windows 10: What does this mean for your business and what steps should you take?
On October 14, 2025, Microsoft will end support for Windows 10. This means that no security updates, bug fixes or […]
Windows Recall – did Microsoft just create the perfect tool to spy on users?
When Microsoft announced the Recall feature for Windows 11 in June 2024, reactions were enthusiastic. The seemingly innocuous option was […]
Thundermail and Thunderbird Pro Services – New Competition for MS 365 and Workspace?
Thundermail and Thunderbird Pro Services – New Competition for MS 365 and Workspace? Mozilla Thunderbird, the popular email client known […]
Secure data in the company – the 3-2-1 rule and effective backup monitoring
Protecting server and database data is the cornerstone of any organization’s security, especially important for companies with their own local […]
How to use the Internet safely?
Using the Internet safely is extremely important these days, when the number of cyber threats is constantly increasing. In order […]
Comparison of Microsoft 365 E5 and Google Workspace Enterprise
Security and Functionality at the Service of Your Organization Our IT company’s primary focus is to provide the highest level […]
A comprehensive guide to implementing S/MIME encryption in an organization
Implementing S/MIME email encryption in an organization is a step toward better data protection and communication security. The process requires […]
Think 2FA is enough? Your MS365 data may need more protection!
Securing MS 365 users in an unsafe environment. Why 2FA alone is not enough and how to strengthen protection with […]
How we implemented Safetica’s DLP system for an HR client
Data protection has become a priority for many companies, especially those in the HR industry, where particularly sensitive employee information […]
Deployment of Stormshield UTM system in a medical wholesaler: Comprehensive data and infrastructure security
Today, as cyber threats become more advanced, companies need to invest in modern technology to protect their data and infrastructure. […]
How we implemented Zero Trust Access Management at one of our clients instead of a VPN
ZTAM Today, IT security is a priority for every company. Traditional methods, such as VPNs, are becoming less and less […]
How to make a mailing? Basics of an effective mailing campaign
Despite the emergence of many new sources of website traffic each year, mailing remains one of the most effective marketing […]
Manufacturing enterprise vs. NIS2? An adaptation guide.
The Network and Information Systems Security Directive (NIS2 ) is an updated version of the European Network and Information Systems […]
Protection of whistleblowers in Poland: Who must comply with the new law?
In Poland, companies and institutions qualify for the Whistleblower Protection Act if they employ at least 50 people or provide […]
The government’s adoption on April 2 of a draft law on whistleblower protection
The Polish government’s adoption of a draft law on the protection of whistleblowers on April 2 marks a milestone on […]
Google Consent Mode v2, a consent mode that is required by the DPA. What does it consist of?
By the end of February 2024, all website owners should implement a new version of consent mode, known as consent […]
IT outsourcing for companies. Do companies opt for it?
The global pandemic has convinced businesses that IT outsourcing is worth exploring. Our company specializes in IT outsourcing for companies […]
IT support- essential qualities and skills of an IT specialist
The IT industry is developing at a rapid pace. IT service in Warsaw is at a very high level. The […]
IT audit Warsaw. What does it consist of?
Cybersecurity – benefit from an IT audit in Warsaw Why is a security audit so important? When a hacker breaks […]
Migration to the cloud – modernizing the operation of the enterprise
What is moving to the cloud Warsaw? Migrating to the cloud is, of course, moving your company’s operations and procedures […]
IT outsourcing – step by step – cost optimization Warsaw
Optimization of IT costs ? You have come to the right place. We will show you what the different types […]
If I own Windows 7, can I upgrade it to Windows 10 for free?
Many sites decry the fact that the automatic license activation after upgrading Windows 7 to Windows 10 still works. And indeed it is enabled but for people who have purchased a BOX version of the key or are disabled.
Types of IT outsourcing
The numerous advantages of IT outsourcing have made this type of IT service increasingly popular with entities in the small, medium and large business sectors. Depending on the size of the company, as well as individual preferences and the scope of the planned service, it is possible to choose from different types.
Facts about outsourcing
Outsourcing, which is gaining in popularity, is growing in popularity for good reason. This form of partnership is a favorable solution for both Principals and Contractors, as evidenced by the following facts:
Szukaj
Kategorie
- Alerts 1
- Case Studies 8
- IT Guide 25
- News 13
- Services 17
- Uncategorized 18
Recent Posts
- Server consolidation – less is more. How to gain in cost, performance and security?
- WIN10 END OF LIFE. End of support for Windows 10: What does this mean for your business and what steps should you take?
- Windows Recall – did Microsoft just create the perfect tool to spy on users?
- Thundermail and Thunderbird Pro Services – New Competition for MS 365 and Workspace?
- Secure data in the company – the 3-2-1 rule and effective backup monitoring
Ostatnie posty
-
 Server consolidation – less is more. How to gain in cost, performance and security?
Server consolidation – less is more. How to gain in cost, performance and security? -
 WIN10 END OF LIFE. End of support for Windows 10: What does this mean for your business and what steps should you take?
WIN10 END OF LIFE. End of support for Windows 10: What does this mean for your business and what steps should you take? -
 Windows Recall – did Microsoft just create the perfect tool to spy on users?
Windows Recall – did Microsoft just create the perfect tool to spy on users? -
Thundermail and Thunderbird Pro Services – New Competition for MS 365 and Workspace?
-
 Secure data in the company – the 3-2-1 rule and effective backup monitoring
Secure data in the company – the 3-2-1 rule and effective backup monitoring
Zapisz się do newslettera
Zapisz się do newslettera Jeton i nie przegap nowości.